Welcome back,
Python is probably the most widely used scripting language for hackers. This is primarily because it has some built-in modules and libraries that make many of the tasks we need to do as hackers much simpler and faster.
In this guide, I want to fill in some more of the basic information about Python and then build a password cracker for an FTP server using some of things we have learned in these three modules.
Dictionaries
In Python, dictionaries act like associative arrays in other languages. We use these when we want to store a list of items (elements) and give them a label. This could be such things as user IDs to names or associating known vulnerabilities to a specific host.
Dictionaries hold unordered pairs, a key and a value, where the keys must be unique. Like lists that I addressed in the previous tutorial, dictionaries are iterable. This means that we can go through them with a control structure such as a for statement, assigning each element of the dictionary to a variable until we come to the end of the dictionary. Among other things, you might use this structure for building a password cracker where we iterate through each password in a dictionary until one works or come to the end. Dictionaries provide fast lookups.
To instantiate a dictionary, the syntax looks like this:
dict = {key1:value1, key2:value2, key3:value3…}
Control Statements
Like any programming or scripting language, often we need our code to make a decision. There are a number of ways in Python to control the flow of the script. For instance, we may want to set a conditional statement that if this.. then that… else do that. Let’s look at some of these structures in Python.
if:
The if structure in Python is similar to the if…then in BASH. The syntax looks like this:

The control block in Python must be indented.
if …else:
The if…else structure in Python is similar to the if…then …else in BASH scripting. The syntax looks like this:

For example, here we have code snippet that checks the value of a user ID, if it is 0, then we print a message “You are root.” Else, if it is any other value, we print the message “You are not root.”

Loops:
Loops are another useful structure in Python. The two must widely used arewhile and for.
while:
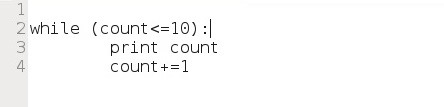
The while statement evaluates a Boolean expression (evaluates to true or false) and continues execution while the expression evaluates to true. For example, we could create a code snippet that prints each number from 1 until 10 and then exits the loop.
for:
The for loop assigns values from a list, string, or other iterable structure such as a dictionary, to loop an index variable each time through the loop. For example we can use a for loop to attempt passwords like in our script below.
Creating an FTP Password Cracker
Now that we have three lessons in Python under our belt, let’s create a simple FTP password cracker in Python. Let’s open a text editor in Kali (I’m using Leafpad) and enter the following script below.
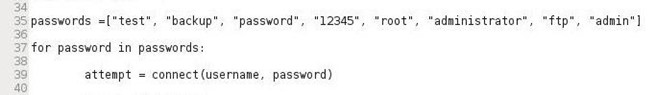
Note that we import the socket, re, and sys modules (Lines 3-7), then create a socket that attempts to connect to specified IP address on port 21 (lines 11-15), then create a variable username which is assigned “NullByte” (Line 33), then create a list called “passwords” with potential passwords (Line 35), then create a for loop trying each password until it receives a code 230 or exhausts the password list.

Of course, you can change the values in this script to any that you want and are appropriate to your circumstances. In future tutorials, we will modify this password cracker to give it even greater usability and versatility.
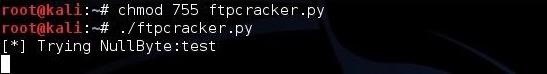
Save it as “ftpcracker.py” and give yourself execute permissions, then run the script against an FTP server.
kali > chmod 755 ftpcracker.py
kali > ./ftpcracker.py
If it finds the password, it will print the message ‘Password found: <password>” (Line 43).
Keep coming back, my novice hackers, as we continue to expand our scripting skills to the level of a pro hacker!
Python is probably the most widely used scripting language for hackers. This is primarily because it has some built-in modules and libraries that make many of the tasks we need to do as hackers much simpler and faster.
In this guide, I want to fill in some more of the basic information about Python and then build a password cracker for an FTP server using some of things we have learned in these three modules.
Dictionaries
In Python, dictionaries act like associative arrays in other languages. We use these when we want to store a list of items (elements) and give them a label. This could be such things as user IDs to names or associating known vulnerabilities to a specific host.
Dictionaries hold unordered pairs, a key and a value, where the keys must be unique. Like lists that I addressed in the previous tutorial, dictionaries are iterable. This means that we can go through them with a control structure such as a for statement, assigning each element of the dictionary to a variable until we come to the end of the dictionary. Among other things, you might use this structure for building a password cracker where we iterate through each password in a dictionary until one works or come to the end. Dictionaries provide fast lookups.
To instantiate a dictionary, the syntax looks like this:
dict = {key1:value1, key2:value2, key3:value3…}
Control Statements
Like any programming or scripting language, often we need our code to make a decision. There are a number of ways in Python to control the flow of the script. For instance, we may want to set a conditional statement that if this.. then that… else do that. Let’s look at some of these structures in Python.
if:
The if structure in Python is similar to the if…then in BASH. The syntax looks like this:

The control block in Python must be indented.
if …else:
The if…else structure in Python is similar to the if…then …else in BASH scripting. The syntax looks like this:

For example, here we have code snippet that checks the value of a user ID, if it is 0, then we print a message “You are root.” Else, if it is any other value, we print the message “You are not root.”

Loops:
Loops are another useful structure in Python. The two must widely used arewhile and for.
while:
The while statement evaluates a Boolean expression (evaluates to true or false) and continues execution while the expression evaluates to true. For example, we could create a code snippet that prints each number from 1 until 10 and then exits the loop.

for:
The for loop assigns values from a list, string, or other iterable structure such as a dictionary, to loop an index variable each time through the loop. For example we can use a for loop to attempt passwords like in our script below.

Creating an FTP Password Cracker
Now that we have three lessons in Python under our belt, let’s create a simple FTP password cracker in Python. Let’s open a text editor in Kali (I’m using Leafpad) and enter the following script below.
Note that we import the socket, re, and sys modules (Lines 3-7), then create a socket that attempts to connect to specified IP address on port 21 (lines 11-15), then create a variable username which is assigned “NullByte” (Line 33), then create a list called “passwords” with potential passwords (Line 35), then create a for loop trying each password until it receives a code 230 or exhausts the password list.

Of course, you can change the values in this script to any that you want and are appropriate to your circumstances. In future tutorials, we will modify this password cracker to give it even greater usability and versatility.
Save it as “ftpcracker.py” and give yourself execute permissions, then run the script against an FTP server.
kali > chmod 755 ftpcracker.py
kali > ./ftpcracker.py

If it finds the password, it will print the message ‘Password found: <password>” (Line 43).
Keep coming back, my novice hackers, as we continue to expand our scripting skills to the level of a pro hacker!
***Buying gift vouchers and cc from dark web guide .***
ReplyDelete