Security breaches can happen to anyone at anytime. You, your family, your doctor’s office, your college, the stores you shop in, the websites you visit, and even the agencies that meet basic needs like water and electricity.
According to a report from the United States Government Accountability Office, The U.S. Computer Emergency Readiness Team reported a 782% increase in cyber incidents.
SRC Cyber released an infographic that depicts some of the most infamous occurrences over the last decade and how they’ve affected the global cyber landscape.
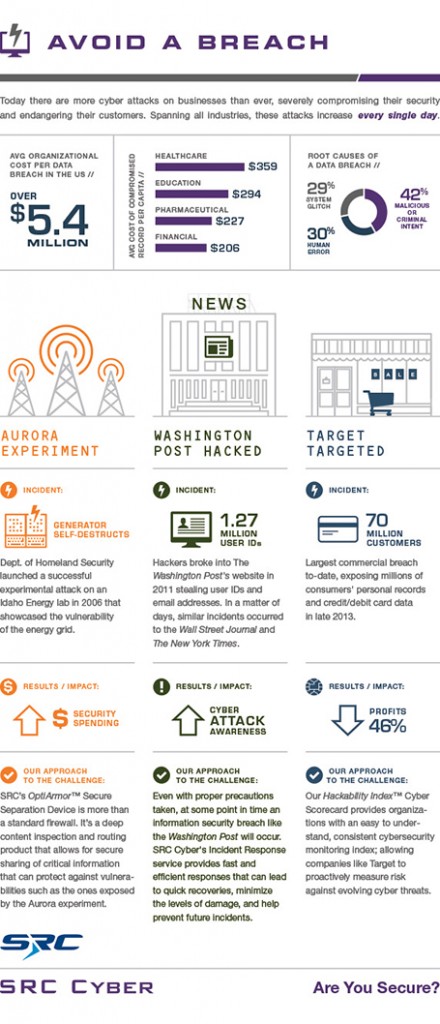
How to Avoid a Data Breach
End User Security Awareness Training
End user security awareness training, when done often, is a huge benefit, but only when it changes the culture of the company to be more security minded. Training insiders helps eliminate mistakes that could lead to a breach, as well as helps them notice odd behavior by malicious insiders or fraudsters.
Craft an Encryption Policy
Laptop theft is the number-one cause of data breaches in 2009, however, there are only four states that require disclosure if that data is not encrypted. Having a good encryption policy that you can enforce on employee laptops is key.
Ensure Physical Security
Ensure proper physical security of electronic and physical restricted data wherever it lives. Lock down workstations and laptops as a deterrent. Secure your area, files and portable equipment before leaving them unattended. Shred sensitive paper records before disposing of them.
Deploy IDS & IPS
Intrusion detection and prevention should be used for all mission-critical systems and systems that are accessible via the Internet, such as Web servers, e-mail systems, servers that house customer or employee data, active directory server, or other systems that are deemed mission critical.
Stop Drive By Downloads – Content Filtering
There are so many breaches that occur via drive-by downloads — malicious or compromised Web sites that can exploit your machine simply by accessing a Web site. Being able to block where insiders go is key to a good security policy.
Perform Regular Vulnerability Assessments
Organizations should perform regular vulnerability assessments. Many companies still only perform vulnerability scans once a quarter. These should be done weekly. Today, organizations should perform vulnerability scans against every system in their network, both internal and external.
Apply comprehensive Patch Management
Every IT person knows about patching, but many still don’t do it comprehensively enough. Many IT people will simply turn on the Microsoft updates and believe everything is good. What about the other operating systems such as Linux, UNIX, Mac? More important are the third-party applications that are not patched by Microsoft, such as Adobe.
System Monitoring – Employ Insider Behaviour Monitoring
Employing a system monitoring program where the HR person or compliance officer can replay the behaviour of an insider is invaluable. Combine that with data loss prevention (DLP) technology where you can set rules and, based on those rules, block content that you do not want to leave the network.
Back it Up
Many breaches are caused by the theft or loss of data backup tapes. A remote data backup service allows the company to use the Internet to back up safely and effectively without ever using tapes that can be lost or stolen.
No comments:
Post a Comment